A lost laptop on a business trip. A single employee clicking the wrong link. A delayed patch that opens a week-long window for attackers. That’s all it takes for sensitive business data to vanish – or worse, be sold.
Yet most companies still rely on antivirus software alone, overlooking the deeper layers of protection that make laptops truly secure.
The truth is, most devices don’t come with everything you need preinstalled – and that’s okay. Security isn’t about what your laptop ships with, but what your IT team sets up, enables, and manages after it arrives.
Some defences are already built into business-grade laptops, others need to be configured or added – but together, they form the foundation every organisation should rely on.
Here’s how to make your laptops security-ready from the inside out.
AI-Powered Endpoint Protection
Because threats evolve faster than definitions.
Traditional antivirus tools detect what they already know. But today’s attacks are polymorphic – they disguise themselves, hide in memory, and move laterally across systems long before signatures are updated.
Modern AI-driven endpoint protection changes the game. Tools like Microsoft Defender for Endpoint, CrowdStrike Falcon, and SentinelOne Singularity learn your system’s behaviour – spotting subtle anomalies in real time.
While the AI itself isn’t built into the laptop hardware, a business-grade device should be capable of running these behavioural defence tools without lag or compatibility issues.
Ensure your laptops can support AI-based endpoint security agents – and that they’re enabled from day one.
Hardware-Enabled Encryption
Protects your data even when your laptop doesn’t.
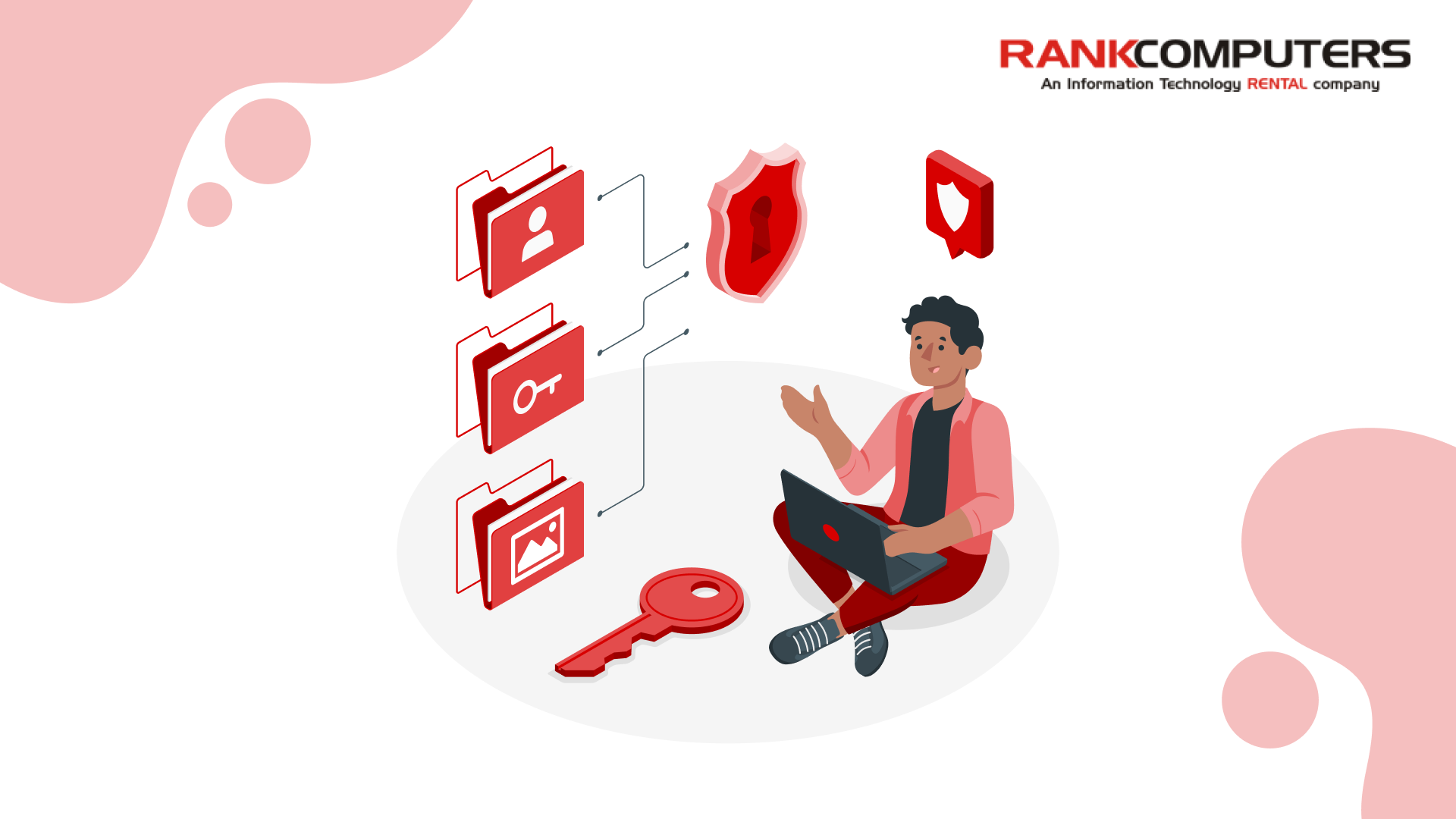
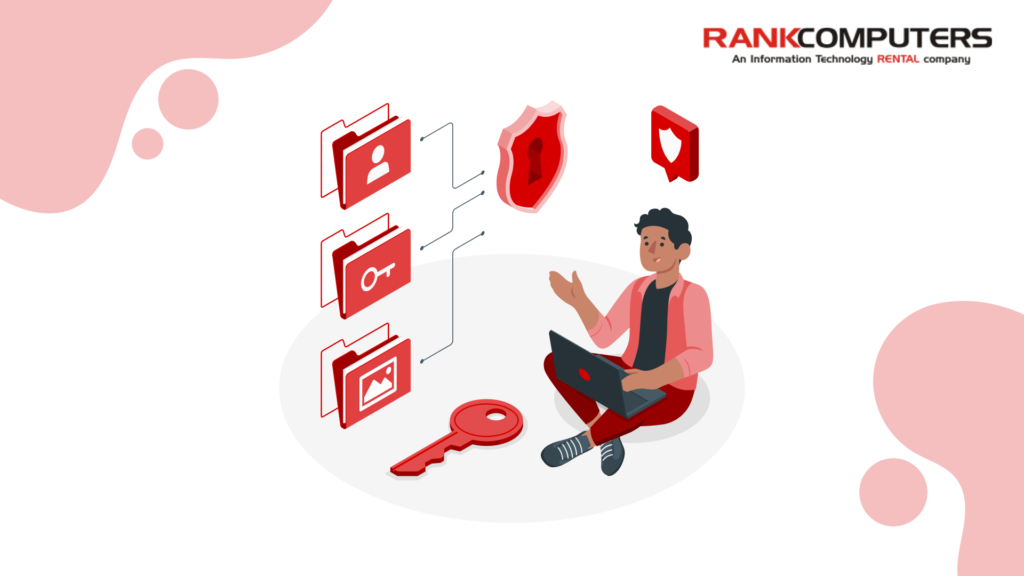
Encryption is your first line of defence when a laptop is lost or stolen. Software-based encryption tools like BitLocker or FileVault work well – but when combined with hardware-enabled encryption, they’re virtually unbreakable.
Modern business laptops often come with a Trusted Platform Module (TPM 2.0) and, in many cases, self-encrypting drives (SEDs) that offload encryption to dedicated chips. This means your data stays locked even if someone removes the drive from the system.
Ask your vendor: Does the laptop include a TPM 2.0 chip, and is full-disk encryption enabled before deployment?
Self-Healing BIOS & Firmware Protection
Because cyberattacks don’t stop at your operating system.
Firmware attacks live below the OS. Once compromised, even reinstalling Windows won’t save you. That’s why many business-grade laptops from HP, Dell, and Lenovo include self-healing BIOS technology.
It constantly verifies the firmware’s integrity and automatically restores it if tampered with.
Even if your laptop doesn’t include this by default, IT teams should ensure firmware protection is available or enabled through vendor management tools.
Trusted Platform Module (TPM) 2.0
The small chip that protects everything.
A TPM chip is like a vault inside your laptop – it securely stores encryption keys, credentials, and certificates, protecting them even if the device is compromised.
Most business laptops today include TPM 2.0, not just for encryption but also for Secure Boot and device attestation.
Windows 11 even requires it, making TPM a must-have for modern compliance.
Remote Management & Data Wipe
When you can’t find the laptop, at least control the data.
Lost devices are inevitable. What matters is your ability to neutralize the risk in minutes.
With remote management tools like Intel vPro, Windows Autopilot, and MDM integrations, IT admins can lock or wipe laptops remotely – no matter where they are. These capabilities aren’t hardware features alone – they require proper setup with enterprise management software.
Endpoint Detection & Response (EDR)
Because antivirus prevention isn’t enough.
EDR doesn’t just block malware – it watches, records, and responds. It tracks unusual behaviour across endpoints, isolating compromised systems automatically and providing digital forensics to understand what went wrong.
Modern laptops are EDR-ready, but the tools themselves – CrowdStrike, Defender, Sophos, or SentinelOne – are software layers. The key is choosing laptops that support continuous monitoring, low-level kernel visibility, and fast response times.
Before You Procure – Ask These 5 Questions
- Is TPM 2.0 enabled on every laptop in our fleet?
- Are drives self-encrypting or encryption-ready?
- Can we remotely wipe or lock any device instantly?
- Is our firmware protected from unauthorized modification?
If any answer makes you hesitate, your defence has a gap.
Security Costs Less When It’s Planned Early
Cutting corners on laptop security might save ₹20,000 today – but a single breach can cost lakhs in penalties, downtime, and lost reputation.
Smart IT teams plan for security upfront – choosing business laptops that support encryption, TPM 2.0, firmware protection, and enterprise management tools from day one.
If buying feels complex, enterprise rental solutions are a faster path.
Rank Computers makes it easy for businesses to access modern, business-grade laptops that are ready for enterprise use – pre-tested, compliant-ready, and performance-optimised for professional workloads. No heavy upfront costs. No long procurement delays.
Renting doesn’t just cut costs; it keeps your fleet current, reduces downtime, and ensures your business always runs on the latest hardware standards.
Because when security and efficiency go hand in hand, planning early always pays off.